Managed Detection and Response Driven by AI & 1,000 Cyber Warriors
Managed detection and response is a combination of technology and skills to deliver advanced threat detection, deep threat analytics, global threat intelligence, faster incident mitigation, and collaborative breach response on a 24×7 basis. However, MDR services are not a replacement of traditional managed security services (MSS) such as log management, log monitoring, vulnerability scanning, and security device management.
Both solutions have a role to play; MDR enhances MSS services with focus on detecting and responding to breaches by bringing in complementary technologies and services on security analytics, response orchestration, and threat intelligence. MDR services can be delivered by specialized vendors focused only on threat management or by an existing MSS provider with Managed detection and response capabilities. For many organizations, the best value comes from working with a single provider who has integrated MSSP and Managed detection and response services. Our MDR service is highly recommended by Gartner.

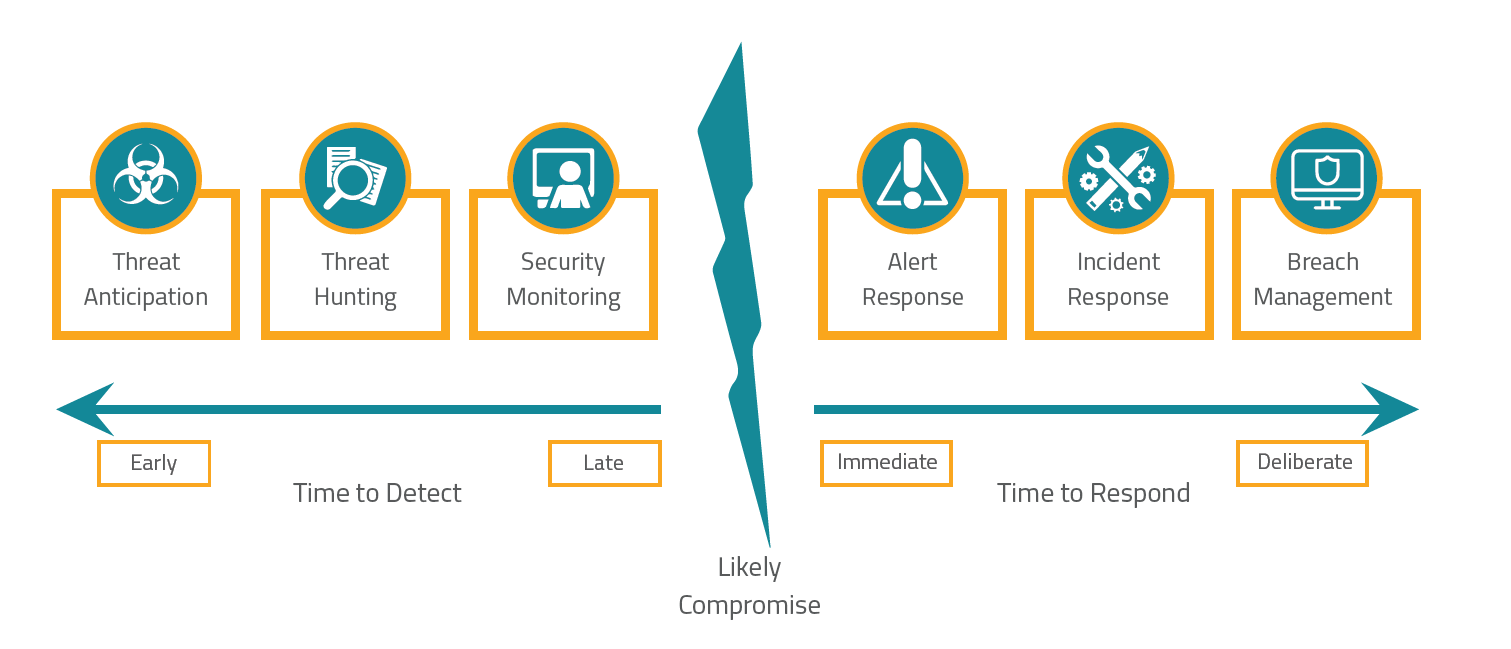
Threat Anticipation
Zero Day vulnerabilities are one of the greatest nightmares that any IT organization has to deal with. Attacks are swift and new vulnerabilities emerge on a daily basis. Threat anticipation powered by Paladion sifts through 100 tb per day of day from sources all over the internet included darknet. This information is gathered, analyzed and remediation suggestions are delivered to you specifically for your network environment.
Threat Hunting
There are two main kinds of attacks which security experts need to deal with, known and unknown. Threat hunting deals specifically with unknown attacks. It does this by analyzing log sources from different points within your network in real time using our big data cloud. The AI behind our analytics tool then determines whether a user is just a user or they have some sort of malicious intent.
Security Monitoring
Our vulnerability playbook as part of our security monitoring service is used for known attacks i.e those attacks which follow a specific pattern. These kinds of attacks are triggered by a unique signature which is detected for each kind of attack. The vulnerability playbook is constantly updated by a team of dedicated security researchers who work tirelessly to keep you protected.
Alert Response
Alter response is all about triaging different alerts to figure out which threat is most relevant. For example a compromised password of the companies CEO is much more important than a potential CSRF vulnerability. In short, not every alter needs an incident response plan to be activated. The alerts need to be investigated for who, what , when and how to determine the extent of the impact.
Incident Response
Response orchestration technology in action, carrying out rapid coordinated activities for the purpose of containment, remediation and recovery. We use our response automation platform; it operates on response work flows, case management, forensic tools and playbooks for a plethora of different incidents. Our response team work with you to contain, mitigate and recover from major incidents leveraging our platform and our knowledge base.
Breach Management
In the unfortunate but inevitable cases whereby a breach does occur, our MDR services assists in the entire breach management of customer confidential data. We provide services based on breach forensics, evidence collection and retention. We will asses the impact on compliance as well as regulatory requirements and best practices for breach notifications.
