Threat Hunting
A Threat Hunting team and a streamlined AI platform that combines network, end-point, application, and user behavior threat analytics to uncover threats and attack campaigns that traditional security monitoring mechanisms miss. Data science and machine learning are used with security, user and IT data to enable the detection of unknown and hidden threats. There are now multiple security analytics technologies in market, including network threat analytics (NTA), user behavior analytics (UBA), endpoint threat analytics/endpoint detection and response (EDR), and application threat analytics (ATA). Our MDR service converts such analytics into actionable outcomes of detecting potential threats that have
bypassed traditional security controls.
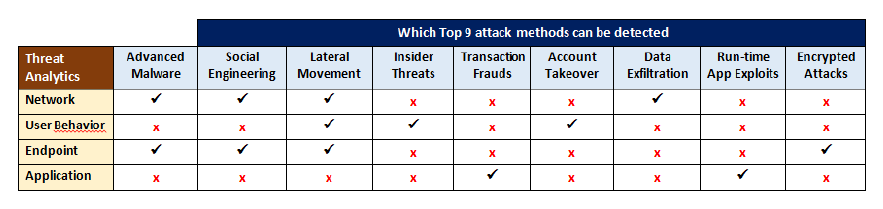
Top 9 Methods for Advanced Threats
1. Advanced Malware
2. Social Engineering
3. Lateral Movement
4. Insider Threats
5. Transaction Fraud
6. Account Takeover
7. Data Exfiltration
8. Run-time App Exploits
9. Encrypted Attacks
What Does Kralanx Offer?
You will benefit from 4 dimensional security analysis which covers networks, end points, users and application threats.
You will get a full analysis spectrum pushed through a single interface which will simplify the process of dealing with these kinds of issues.
High speed detection looks at the full attack kill chain to ensure that you are fully covered.
Our threat hunting team have an organized approach to engage with your MSSP or SOC.
